Drive secure
Author: h | 2025-04-24
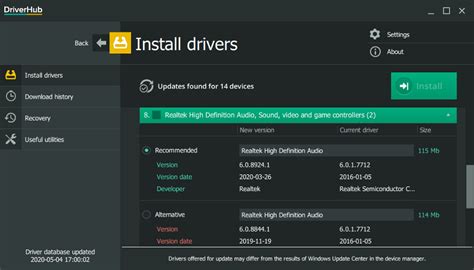
Secure-enabled drives are used with the Drive Security feature. When you enable the Drive Security feature and then apply Drive Security to a pool or volume group on secure-capable drives, the drives become secure-enabled. Read and write access is available only through a controller that is configured with the correct security key.
Is Google Drive Secure? Learn about Google Drive Security
Managing Storage Adapters This chapter includes the following sections: Managing Storage Adapters Self Encrypting Drives (Full Disk Encryption) Cisco IMC supports self encrypting drives (SED). A special hardware in the drives encrypts incoming data and decrypts outgoing data in real-time. This feature is also called Full Disk Encryption (FDE). The data on the drive is encrypted on its way into the drive and decrypted on its way out. However, if you lock the drive, no security key is required to retrieve the data. When a drive is locked, an encryption key is created and stored internally. All data stored on this drive is encrypted using that key, and stored in encrypted form. Once you store the data in this manner, a security key is required in order to un-encrypt and fetch the data from the drive. Unlocking a drive deletes that encryption key and renders the stored data unusable. This is called a Secure Erase. The FDE comprises a key ID and a security key. The FDE feature supports the following operations: Enable and disable security on a controller Create a secure virtual drive Secure a non-secure drive group Unlock foreign configuration drives Enable security on a physical drive (JBOD) Clear secure SED drives Clear secure foreign configuration Scenarios to consider While Configuring Controller Security in a Dual or Multiple Controllers Environment Note Dual or Multiple controllers connectivity is available only on some servers. Controller security can be enabled, disabled, or modified independently. However, local and remote key management applies to all the controllers on the server. Therefore security action involving switching the key management modes must be performed with caution. In a scenario where both controllers are secure, and you decide to move one of the controllers to a different mode, you need to perform the same operation on the other controller as well. Consider the following two scenarios: Scenario 1—Key management is set to remote; both controllers are secure and use remote key management. If you now wish to switch to local key management, switch the key management for each controller and disable remote key management. Scenario 2—Key management is set to local; both controllers are secure and use local key management. If you now wish to switch to remote key management, enable remote key management and switch the key management for each controller. If you do not modify the controller security method on any one of the License: All 1 2 | Free Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick software converts your USB flash Drive into a personal vault and the key to access and Secure your private files. Encrypt-Stick requires a serial numbered USB flash Drive to run. It gives you the ability to create unlimited invisible encrypted... Category: Security & Privacy / EncryptingPublisher: ENC Security Systems Inc., License: Freeware, Price: USD $0.00, File Size: 12.9 MBPlatform: Mac Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick software converts your USB flash Drive into a personal vault and the key to access and Secure your private files. Encrypt-Stick requires a serial numbered USB flash Drive to run. It gives you the ability to create unlimited invisible encrypted... Category: Security & Privacy / EncryptingPublisher: ENC Security Systems Inc., License: Freeware, Price: USD $0.00, File Size: 3.7 MBPlatform: Windows Odin HDD Encryption is a powerful Hard Disc Drive Encryption software which can protect,secure,encrypt your hard disc drive,virtual hard disk(VHD),USB flash files,removable drive. Odin HDD Encryption is a powerful Hard Disc Drive Encryption software which can protect,Secure,Encrypt your hard disc Drive,virtual hard disk(VHD),USB flash files,removable Drive.It can makes a part or all your hard disc into a Secure vault.And it also can creates a virtual encrypted disk within a fileSecure Drive Software Informer: P-Encrypt Secure Drive is a
Quick Links Why "Secure Delete" Options Were Created How Secure File Deletion Tools Work Why They Don't Work Reliably Some utilities have a "secure delete" option that promises to securely erase a file from your hard drive, removing all traces of it. Older versions of Mac OS X have a "Secure Empty Trash" option that tries to do something similar. Apple removed this feature recently because it just doesn't work reliably on modern drives. The problem with "secure delete" and "secure empty trash" is that it provides a false sense of security. Rather than relying on these sorts of bandaid file-deletion solutions, you should rely on full-disk encryption. On a fully encrypted disk, both deleted and undeleted files are protected. Why "Secure Delete" Options Were Created Traditionally, deleting a file from a mechanical hard drive didn't actually delete that file's contents. The operating system would mark the file as deleted, and the data would eventually be overwritten. But that file's data was still sitting on the hard drive, and file-recovery tools could scan a hard disk for deleted files and recover them. This is still possible on USB flash drives and SD cards, too. If you have sensitive data -- for example, business documents, financial information, or your tax returns -- you might worry about someone recovering them from a hard drive or removable storage device. "Secure delete" utilities attempt to solve this problem by not just deleting a file, but overwriting the data with either zeros or random data. This should, the theory goes, make it impossible for someone to recover the deleted file. This is sort of like wiping a drive. But, when you wipe a drive, the enter drive is overwritten with junk data. When you securely delete a file, the tool attempts to overwrite only that file's current location with junk data. Tools like this are available all over the place. The popular CCleaner utility contains a "secure delete" option. Microsoft offers an "sdelete" command for download as part of the SysInternals suite of utilities. Older versions of Mac OS X offered "Secure Empty Trash", and Mac OS X still offers an included "srm" command for securely deleting files. Why They Don't Work Reliably The first problem with these tools is that they'll only attempt to overwrite the file in its current location. The operating system may have made backup copies of this file in a. Secure-enabled drives are used with the Drive Security feature. When you enable the Drive Security feature and then apply Drive Security to a pool or volume group on secure-capable drives, the drives become secure-enabled. Read and write access is available only through a controller that is configured with the correct security key. Open Quick Heal Total Security. On the left pane, navigate to Protection External Drive Protection Secure Removable Drives . In Secure Removable Drives, click the icon to secure removable drives.Is Google Drive Secure? How Secure Is Google Drive? - MiniTool
Related to hard drive errors, ensuring data integrity and preventing potential data loss. Complementing this is the Disk Cleaner, which efficiently removes unnecessary files, freeing up ... Freeware tags: cleaner, shutdown timer, disk checker, splitter, Puran Software, file recovery, performance enhancement, disk cleanup, download Puran Utilities, registry cleaner, system optimization, recovery, eraser, Puran Utilities, Puran Utilities free download Active@ ERASER 4.1.0.7 Active@ ERASER keeps your system secure from undesired data recovery. ... Logical Drives, supports IDE / ATA / SCSI hard disk drives, large (more than 128GB) size drives, HDD ... It can be placed and run from USB Disk, erases Internet Activities (temporary internet files, cookies, history, ... Shareware | $29.95 tags: eraser, keep secure, data recovery, securely owerwrites, FAT12, FAT16, FAT32, NTFS, NTFS 5, file systems, unformat, active undelete, deleted, formatted files, LSoft technologies ShredIt for Windows 6 ... be recovered. Whether you want to erase a hard drive or wipe a file, ShredIt for Windows ... software for the job. It shreds files, folders, disk free space, hard drives and external hard drives. ... Shareware | $24.95 tags: data, file, shredder, free space, disk, hard disk, hard drive, deleted, wipe, erase, shred, privacy, secure, delete, permanently, permanent, remove, already deleted, recycle bin, destruction, cleaner, eraser KillDisk Industrial 6.0.7.0 ... applications where it's often necessary to wipe multiple hard drives simultaneously. Supporting the parallel erasure of upwards of 100 connected devices, this software is intended to be used on its ... Data Only | $455.00 tags: killdisk industrial, killdisk, hard drive eraser, hdd eraser, ssd eraser, data sanitization, disk sanitizer, hard drive sanitizer, wipe multiple hard drives, erase multiple hard drives, secure erase ssd, secure eraser, secure delete ByebyeData Eraser Free Edtition 1.13.0 Free hard drive eraser ByebyeData Eraser to erase hard drives, files, and folders. Free data destruction software to make disk clean. Free hard drive wipe software to clear hard drive and ... Freeware ByebyeData Eraser Pro for Business Edtit 1.13.0 ... boot CD to erase boot drive in ByebyeData Eraser Pro for Business Edition in commercial use. Pro ... for home edition, which is capable Areas while Enhanced Secure Erase goes further by writing predetermined data patterns to every sector on the drive. So Secure Erase provides a quick and secure way to wipe a drive without needing to erase it bit-by-bit.The effectiveness of Secure Erase has been debated, so it may not be approved for sanitizing drives with highly sensitive data. But for most use cases, it provides adequate protection against data recovery. Just be sure to confirm your drive supports the Secure Erase command before relying on it as a wiping method.Limitations and PrecautionsWhile methods like secure erase commands and degaussing can be effective for traditional hard disk drives (HDDs), they have some important limitations when applied to solid-state drives (SSDs). SSDs store data differently than HDDs, making secure erase commands less reliable at permanently wiping all data (Source).With SSDs, you also have to contend with data remanence, where traces of deleted files may still be recoverable due to how the drive handles file deletion and garbage collection (Source). Wear leveling techniques used in SSDs further complicate data erasure. External drive enclosures designed for HDDs may also not fully support SSDs.To reliably wipe an SSD without a computer, methods like degaussing or physical destruction via drills or shredders may be better options. However, you need the proper equipment to safely dismantle the drive enclosure and access the internal components. It’s also wise to take precautions against data remanence by using multiple overwrite passes.In summary, while many data wiping solutions exist, fully and securely erasing an SSD without a host computer involves some unique challenges. Understanding the limitations of various methods can help guide the ideal approach.ConclusionRecap main points, hard drive wiping is possible without a computer but has challenges. In summary, while wiping a hard drive without a traditional computer is possible through methods like external enclosures, standalone erasers, degaussing tools, and physical destruction, it comes with certain limitations. The process can be more time-consuming, technically challenging, and less thorough compared to using wiping software on a full computer. However, for situations where a computer is not available or the drive needs to be permanently destroyed, these techniques allow deleting data securely. Just be mindful of their restrictions. With proper precautions, physical destruction may be the most foolproof way to sanitize a drive without a typical PC setup. While doable, wiping a disk without a computer takes more effort and care. But whenDrive Secure - Download.com.vn
Roll over image to zoom 32GB Fingerprint Secure USB 3.0 Flash Drive with AES 256 Hardware Encryption – Silver Product Number: 70367Keep data security at your fingertips with the Fingerprint Secure USB drive. Using your fingerprint and powerful hardware-based 256-bit AES encryption, this drive keeps your data safe from unauthorized access, without you having to remember a password. Able to register up to 6 fingerprints, the Fingerprint Secure drive comes with a user management app, letting you manage your fingerprint access with ease. The USB 3.0 interface offers faster data transfer speeds versus USB 2.0 making it easy to transfer multiple files at once or larger files without error. The Verbatim Fingerprint Secure USB 3.0 Drive is backed by a limited lifetime warranty. 256-bit AES hardware data encryption secures confidential dataHardware-based encryption means all encryption is done on the drive – your data is safe even if your drive is stolenFast hardware encryption lets you get up and goUnlock using just your fingerprint with no password requiredRegister up to 6 fingerprintsIncludes user management application to manage fingerprint accessUSB 3.0 performance with USB 2.0 compatibilityLimited lifetime warranty Compatibility: Windows 7 and higher; Mac OS 10.13 and higher Product Number: 70367Capacity/Speed: 32GBHard Drive Security Software - Free Download Hard Drive Security
But if you do, a secure flash drive with a keypad is the way to go. Kingston’s Data Traveler 4000 G2 needs to be unlocked from the computer it’s connected to. The key isn’t this long, that’s the cap attached on the back.DesignIf it weren’t for the label and a slightly heftier feel, you couldn’t tell the Data Traveler 4000 G2 from a non-secure USB thumb drive. The drive is divvied up into a 16MB portion that emulates a CD containing the installer for Windows, OS X, and Linux, and the data partition, which becomes available after you create and enter a password.The software is simple, elegant and seems secure. However, I think it should have a secure virtual keyboard for entering data when you suspect or are worried that your keystrokes are being logged.The Aegis Secure Key 3.0 is a bit larger than your normal flash thumb drive. That’s to accommodate a usably sized keypad, which in this case consists of two columns of number keys (0-9), a lock button, an unlock button, and three status lights (red, green and blue).The keypad runs off of a rechargeable battery when the drive is out of the USB port. This is a must—accessing the keypad when the drive is inserted into a USB port can be awkward or worse.By using a combination of the unlock/lock buttons and the keypad you can define admin and user passwords, reset the drive, and obviously—enter PIN codes (or 7 to 16 digits) to access the. Secure-enabled drives are used with the Drive Security feature. When you enable the Drive Security feature and then apply Drive Security to a pool or volume group on secure-capable drives, the drives become secure-enabled. Read and write access is available only through a controller that is configured with the correct security key.Securely share a Drive file with Virtru Secure Share for Google Drive
6: Mount the SSD: Create a mount point: sudo mkdir /mnt/myssd, Mount the SSD: sudo mount /dev/sdb1 /mnt/myssd, Remember to replace /dev/sdb1 with your SSD's partition name. FAQ: KSD-012010-001-15 There are a variety of external enclosures available on the market. While Kingston aims to be compatible with all system types, occasionally, there may be an incompatibility. If you continue to have trouble with your external SSD enclosure, you may want to try a different enclosure. FAQ: KSD-012010-001-18 Secure Erase User Guide for LinuxThis guide will walk you through securely erasing your Kingston SSD using Linux tools.SATA Secure Erase ProcedureWarningPlease make sure to have a full backup of any important data before you proceed!PrerequisitesYou must have root privileges.You must have your SSD connected to the system as a secondary (non-OS) drive.You must have lsscsi and hdparm installed. You may need to install them with your distribution’s package manager.Your drive must not be in a security freeze.Your drive must not be password protected.Instructions 1. Find the device name (/dev/sdX) of the drive you wish to erase:# lsscsi2. Make sure drive security is not frozen:# hdparm -I /dev/sdX | grep frozenIf the output shows "frozen" (instead of "not frozen") then you cannot continue to the next step. You must try to remove the security freeze by trying one of the following methods:Method 1: Put the system to sleep (suspend to RAM) and wake it up. On most distributions the command to suspend is:# systemctl suspendNow issue the hdparm command again. If it worked the output will show "not frozen" (instead of "frozen").Method 2: Hot plug the drive. This is done by physically unplugging the SATA power cable from the drive and plugging it back in while the system is powered on. You may need to enable hot plug in BIOS. Not all systems support hot plug.Now issue the hdparm command again. If it worked the output will show "not frozen" (instead of "frozen").3. Set a user password on the drive. The password can be anything. Here we are setting the password to "p":# hdparm --security-set-pass p /dev/sdX4. Issue the secure erase command to the drive using the same password: 1234567890 - 1234567890 -# hdparm --security-erase p /dev/sdXThis command may take a few minutes to complete. The drive password is removed upon successful completion.If the secure erase is interrupted or otherwise fails your drive may become security locked. In this case you can remove the security lock using the command below and then try the secure erase procedure again:# hdparm --security-disable p /dev/sdXSATA Secure Erase ExampleNVMe Secure Erase ProcedureWarningPlease make sure to have a full backup of any important data before you proceed!PrerequisitesYou must have root privileges.You must have your SSD connected to the system as a secondary (non-OS) drive.You must have nvme-cli installed. You may need to install it with your distribution’s package manager.Your drive must not be password protected.Instructions1. Find the device name (/dev/nvmeXn1) of the drive you wish to erase:# nvme list 2. Issue the format command to the drive. HereComments
Managing Storage Adapters This chapter includes the following sections: Managing Storage Adapters Self Encrypting Drives (Full Disk Encryption) Cisco IMC supports self encrypting drives (SED). A special hardware in the drives encrypts incoming data and decrypts outgoing data in real-time. This feature is also called Full Disk Encryption (FDE). The data on the drive is encrypted on its way into the drive and decrypted on its way out. However, if you lock the drive, no security key is required to retrieve the data. When a drive is locked, an encryption key is created and stored internally. All data stored on this drive is encrypted using that key, and stored in encrypted form. Once you store the data in this manner, a security key is required in order to un-encrypt and fetch the data from the drive. Unlocking a drive deletes that encryption key and renders the stored data unusable. This is called a Secure Erase. The FDE comprises a key ID and a security key. The FDE feature supports the following operations: Enable and disable security on a controller Create a secure virtual drive Secure a non-secure drive group Unlock foreign configuration drives Enable security on a physical drive (JBOD) Clear secure SED drives Clear secure foreign configuration Scenarios to consider While Configuring Controller Security in a Dual or Multiple Controllers Environment Note Dual or Multiple controllers connectivity is available only on some servers. Controller security can be enabled, disabled, or modified independently. However, local and remote key management applies to all the controllers on the server. Therefore security action involving switching the key management modes must be performed with caution. In a scenario where both controllers are secure, and you decide to move one of the controllers to a different mode, you need to perform the same operation on the other controller as well. Consider the following two scenarios: Scenario 1—Key management is set to remote; both controllers are secure and use remote key management. If you now wish to switch to local key management, switch the key management for each controller and disable remote key management. Scenario 2—Key management is set to local; both controllers are secure and use local key management. If you now wish to switch to remote key management, enable remote key management and switch the key management for each controller. If you do not modify the controller security method on any one of the
2025-04-21License: All 1 2 | Free Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick software converts your USB flash Drive into a personal vault and the key to access and Secure your private files. Encrypt-Stick requires a serial numbered USB flash Drive to run. It gives you the ability to create unlimited invisible encrypted... Category: Security & Privacy / EncryptingPublisher: ENC Security Systems Inc., License: Freeware, Price: USD $0.00, File Size: 12.9 MBPlatform: Mac Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick is the most advanced portable security application available on the market today. Encrypt-Stick software converts your USB flash Drive into a personal vault and the key to access and Secure your private files. Encrypt-Stick requires a serial numbered USB flash Drive to run. It gives you the ability to create unlimited invisible encrypted... Category: Security & Privacy / EncryptingPublisher: ENC Security Systems Inc., License: Freeware, Price: USD $0.00, File Size: 3.7 MBPlatform: Windows Odin HDD Encryption is a powerful Hard Disc Drive Encryption software which can protect,secure,encrypt your hard disc drive,virtual hard disk(VHD),USB flash files,removable drive. Odin HDD Encryption is a powerful Hard Disc Drive Encryption software which can protect,Secure,Encrypt your hard disc Drive,virtual hard disk(VHD),USB flash files,removable Drive.It can makes a part or all your hard disc into a Secure vault.And it also can creates a virtual encrypted disk within a file
2025-04-18Quick Links Why "Secure Delete" Options Were Created How Secure File Deletion Tools Work Why They Don't Work Reliably Some utilities have a "secure delete" option that promises to securely erase a file from your hard drive, removing all traces of it. Older versions of Mac OS X have a "Secure Empty Trash" option that tries to do something similar. Apple removed this feature recently because it just doesn't work reliably on modern drives. The problem with "secure delete" and "secure empty trash" is that it provides a false sense of security. Rather than relying on these sorts of bandaid file-deletion solutions, you should rely on full-disk encryption. On a fully encrypted disk, both deleted and undeleted files are protected. Why "Secure Delete" Options Were Created Traditionally, deleting a file from a mechanical hard drive didn't actually delete that file's contents. The operating system would mark the file as deleted, and the data would eventually be overwritten. But that file's data was still sitting on the hard drive, and file-recovery tools could scan a hard disk for deleted files and recover them. This is still possible on USB flash drives and SD cards, too. If you have sensitive data -- for example, business documents, financial information, or your tax returns -- you might worry about someone recovering them from a hard drive or removable storage device. "Secure delete" utilities attempt to solve this problem by not just deleting a file, but overwriting the data with either zeros or random data. This should, the theory goes, make it impossible for someone to recover the deleted file. This is sort of like wiping a drive. But, when you wipe a drive, the enter drive is overwritten with junk data. When you securely delete a file, the tool attempts to overwrite only that file's current location with junk data. Tools like this are available all over the place. The popular CCleaner utility contains a "secure delete" option. Microsoft offers an "sdelete" command for download as part of the SysInternals suite of utilities. Older versions of Mac OS X offered "Secure Empty Trash", and Mac OS X still offers an included "srm" command for securely deleting files. Why They Don't Work Reliably The first problem with these tools is that they'll only attempt to overwrite the file in its current location. The operating system may have made backup copies of this file in a
2025-03-28